Authors: Han Goossens – Commercial Manager Xebia Security & Tom Rijgersberg, Business Unit Manager Xebia Security
Winning businesses innovate and that innovation will more and more be driven by fast ‘deployment’ of products and services with small increments. Will the drive to reduce time to market for releasing new applications go hand in hand with the growing desire for security? Nowadays a lot of companies experience Security as the biggest impediment in delivering innovation. For the sake of becoming a successful and reliable innovator the next level in the maturity model has been announced: continuous security. What is the relation between Innovation and Security, and more specifically, Application Security? How can organizations successfully apply Continuous Security?
Security versus innovation: Why they are intertwined
Until now, companies haven't fully realized that successful innovation is closely tied to the value of its corresponding digital assets. They even neglected to put them on their balance sheets. But losing these assets through security attacks could prove catastrophic for a company’s innovation success. Too frequently, IT security becomes a top priority only after an enterprise experiences a damaging breach. Cyber criminals endanger business continuity and hack IT for the gain of others. They can creatively exploit secrets, steal money, and encrypt assets for blackmail. Even today, many sacrifice security for the sake of innovation. In ranking considerations of performance, security, maintainability, and scalability, companies prioritized security second to application performance, and most find it difficult to embed (DZone Application and Data Security Survey 2016).
Laws and regulation will start enforcing compliance for security and privacy purposes. Also, end users are becoming more aware of privacy concerns and will demand reliable products with security and privacy in mind. It is no more than logical that organizations will prioritize Security within their innovation efforts.
Reducing vulnerabilities in web applications and APIs
Companies are hungry to adopt any new technology that allows them to differentiate, reduce time to market and decrease cost. But if the technology is not designed or adapted with security and privacy in mind, it opens the door to security breaches and threats. The lack of application security is already the leading cause of breaches and every web application and API has serious vulnerabilities (source).
Security and innovation should go hand in hand. When applying Continuous Security the right way, it will:
- Reduce costs;
- Reduce liabilities;
- Reduce time to market;
- Strengthen brands as reliable.
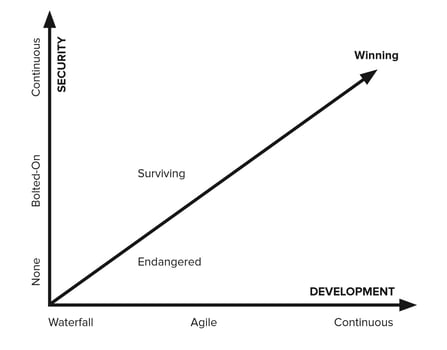
Nowadays, if security impedes innovation, it will be bypassed. For example, fixing security bugs during design is 1/60 of the cost of a patch after the release. It’s really a win-win situation.
Privacy by design
Privacy by design is based on 7 “foundational principles”:
- Proactive not reactive; Preventative not remedial
- Privacy as the default setting
- Privacy embedded into design
- Full functionality – positive-sum, not zero-sum
- End-to-end security – full lifecycle protection
- Visibility and transparency – keep it open
- Respect for user privacy – keep it user-centric
Increased Demand for compliance
Methods like Agile & DevOps have surpassed traditional software development approaches and have delivered on their promises, as many successful businesses can attest. They belong in the “efficiency and effectiveness of operations” category of widely used COSO’s (The Committee of Sponsoring Organizations of the Treadway Commission @ http://www.coso.org/IC.htm) internal control framework. It comes to no surprise that that model also has the category “compliance with laws and regulations”. This category, as said, will become more evident in organizations.
A perfect example, next to the existing Dutch regulations, is the upcoming General Data Protection Regulation (GDPR). It is a regulation by which the European Parliament, the European Council and the European Commission intend to strengthen and unify data protection for individuals within the European Union. This regulation was adopted on 27 April 2016. It enters into application 25 May 2018 after a two-year transition period.
Also catching up are customers privacy concerns as mainstream media report on hacks everyday. That will drive the call for regulation even further. Nowadays insurance companies are starting to offer security insurances as well but they will demand appropriate security measures in return.
Five Principles of Continuous Security
We see continuous security as a discipline that consists of the following five principles:
- Clear roles and responsibilities for security stakeholders and Product Owners;
- Security by design (see Security by design);
- Privacy by design (see Privacy by design);
- Software developers understand how to implement security best practices with respect to examples like cryptography and data validation;
- Software security testing is optimized by applying automation where appropriate and possible.
Secure by design in software engineering, means that the software has been designed from the ground up to be secure. Malicious practices are taken for granted and care is taken to minimize impact when a security vulnerability is discovered or on invalid user input. Threat Modelling is an important part of this.
Developing Continuous Security
Innovation rely on modern development frameworks that depend heavily on automation and an “everything is code” philosophy. Security and privacy, on the other hand, still rely heavily on humans and manual activities. Frontrunners don’t hold on to old school “tick-in-a-box”security checks but develop continuous security the way they develop new business success: through exploration and step-by-step alignment of people, processes, and technology with an agile and pragmatic attitude.
Rest assured, don’t try to encompass it all in one go. Let the five principles of Continuous Security guide you and take small pragmatic and wise steps and you will be ahead of the curve.
This article is part of the Urgent Future IT Forecast 2017.







